National Counterintelligence and Security Center
Forms
Form SF 312:
Classified Information Nondisclosure Agreement
(GSA library link may reflect 2013 version until GSA completes update to the DNI approved 2023 version)
Form SF 714:
Financial Disclosure Report
Current revision date 07/2022
Roles & Responsibilities
The Director of National Intelligence (DNI), in accordance with EO 13467, is responsible, as the Security Executive Agent (SecEA), for the development, implementation, and oversight of effective, efficient, and uniform policies and procedures governing the conduct of investigations and adjudications for eligibility for access to classified information and eligibility to hold a sensitive position. While the DNI is focused primarily on the Intelligence Community (IC), as SecEA his responsibilities are further extended to cover personnel security processes within all agencies, government-wide.
The Special Security Directorate (NCSC/SSD), NCSC’s Special Security Directorate serves as the Executive Staff for all Security Executive Agent functions and responsibilities on behalf of the DNI.
The Suitability and Security Clearance Performance Accountability Council (PAC) is responsible to the President for driving implementation of the Security and Suitability Reform Effort and for “ensuring accountability by agencies, ensuring the Suitability Executive Agent and the Security Executive Agent align their respective processes, and sustaining reform momentum.”
Executive Order 12333 as Amended, 30 July 2008 (PDF)
Goals, Directions, Duties, Responsibilities and Conduct with respect to the United States Intelligence Efforts.
Reforms the Intelligence Community and creates the Director of National Intelligence.
Establishes the National Counterintelligence Executive, the National CI Policy Board, and the Office of the National Counterintelligence Executive with title IX of the FY 2003 Intelligence Authorization Act.
Authorized intelligence and intelligence-related activities for FY 2003.
Reforms the Intelligence Community and creates the Director of National Intelligence.
Authorized intelligence and intelligence-related activities for FY 2004.
Authorized intelligence and intelligence-related activities for FY 2005.
"Uniting and strengthening America by providing appropriate tools required to intercept and obstruct terrorism."
Statutes
Presidential Issuances
National Policies
Intelligence Community Directives
Intelligence Community Policy Guidance
Intelligence Community Standards
- ICS 705-01: Physical and Technical Security Standards for Sensitive Compartmented Information Facilities, 17 September 2010 (PDF)
- ICS 705-02: Standards for the Accreditation and Reciprocal Use of Sensative Compartmented Information Facilities, 22 December 2016 (PDF)
- ICS 706-01: Domestic Facility Security Risk Assessments Standards, 18 June 2019 (PDF)
- New - ICS 706-02: Protecting Mission Critical-Facility Related Control Systems(MC-FRCS) in Mission Critical Facilities(MCF), 23 December 2019 (PDF)
- New - ICS 731-02: Supply Chain Threat Revisions, 25 September 2019 (PDF)
Additional Links
- IC Technical Specifications for Construction and Management of Sensitive Compartmented Information Facilities, v1.5.1 (PDF)
- Aircraft UAV Checklist v1.5 (PDF)
- Cancellation of SCIF Co-Use Joint-Use v1.5 (PDF)
- Construction Security Plan v1.5 (PDF)
- Inspectable Materials Checklist v1.5 (PDF)
- SCIF Compartmented Area (CA) Fixed Facility Checklist v1.5 (PDF)
- SCIF Co-Use Joint-Use Request Users Guide v1.5 (PDF)
- SCIF Co-Use Joint-Use Request v1.5 (PDF)
- SCIF Fixed Facility Checklist v1.5 (PDF)
- SCIF Pre-Construction Checklist v1.5 (PDF)
- SCIF TEMPEST Checklist v1.5 (PDF)
- Shipboard Checklist v1.5 (PDF)
- Submarine Checklist v1.5 (PDF)
- Office of the Director of National Intelligence Policies
- Committee on National Security Systems Issuances
- Technical Specifications for Construction and Management of Sensitive Compartmented Information Facilities, 28 September 2017 (PDF)
Supply Chain Risk Management
We are delighted to announce that the Office of the Director of National Intelligence's (ODNI) National Counterintelligence and Security Center (NCSC) has opened registration for the 2025 Supply Chain Security Technical Symposium.
As we continue to develop new and increasingly connected technologies, secure and resilient supply chains are at the forefront of discussions regarding both economic prosperity and national security. While many emerging technological trends, like developments in artificial intelligence and quantum computers, promise new security solutions, they also introduce their own risks and vulnerabilities as attack surfaces expand, critical resources are constrained, and global supply chains become ever more complex.
ODNI's 2025 symposium will be held in Northern Virginia which will be open to academia industry on the first day of the event, 8 April 2025. The symposium will bring together experts, practitioners, visionaries, and thought leaders from the Intelligence Community (IC), Department of Defense (DoD), international partners, commercial industry, defense industrial base, and academia to explore critical issues related to cyber supply chain security, and to provide actionable insights and recommendations to IC and DoD leadership. Attendees will have unique access to the people and technologies that are transforming the future of supply chain security.
To register, please reach out to SAIC at This email address is being protected from spambots. You need JavaScript enabled to view it..
Mission Statement
The mission of NCSC's Supply Chain and Cyber Directorate (SCD) is to enhance the nation's supply chain and cyber security, leveraging multidisciplinary counterintelligence and security expertise to inform, guide, and coordinate integrated risk decisions and responses with strategic partners.
PROTECTING CRITICAL SUPPLY CHAINS

A Guide to Securing Your Supply Chain Ecosystem

Building a Resilient Ecosystem
Protecting Critical Supply Chains: Risks From Adversarial Exposure

Protecting Critical Supply Chains: Cyber Threat Hunting
CHAMPION SUPPLY CHAIN
Take the General Services Administration (GSA) and Federal Acquisition Institute (FAI) training course to Fortify the Chain:
- FAC-093: "Introduction to Supply Chain Risk Management"
- Requires Defense Acquisition University (DAU) account or Department of Defense (DoD) Common Access Card (CAC)
Protecting Supply Chains for Critical Technologies
In October 2021, the National Counterintelligence and Security Center (NCSC) prioritized outreach efforts in five critical technology sector areas: Artificial Intelligence (AI), Bioeconomy, Autonomous Systems, Quantum, and Semiconductors.
These technologies present unique opportunities and challenges where the stakes are potentially greatest for U.S. economic and national security.
One of the unique challenges is managing the threats and risks to the very complex supply chains that support each one of these critical and emerging technologies.
For National Supply Chain Integrity Month in April 2022, NCSC focused on supply chain security issues unique to AI, specifically machine learning (ML) an AI subset; autonomous systems, specifically autonomous vehicles; and semiconductors
The awareness materials below highlight the unique supply chain issues associated with these critical technologies.
- Autonomous Automotive Vehicle Supply Chain Risk
- Information and Communications Technology and the Supply Chain Risk
- Managing Supply Chain Risk to Machine Learning
- Supply Chain Risks to Semiconductors
National Supply Chain Integrity Month
April 2024—#SCRM is the A.C.E.
Don't let threat actors have the upper hand.
Play an A.C.E.
- Acquisition Security
- Cyber Security
- Enterprise Security
- Press Release — April 2024 National Supply Chain Integrity Month
- Supply Chain Integrity Month Calendar
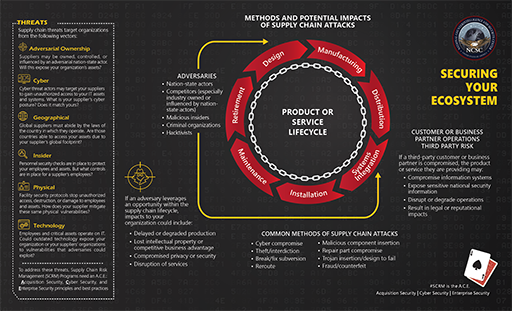
Securing Your Ecosystem: Methods and Potential Impacts of Supply Chain Attacks
April 2023 — Supply Chain Risk Management (SCRM) – The Recipe for Resilience
- Zero-Trust Architecture
- Software Supply Chain Attacks
- Critical Minerals Supply Chain Resilience
- 5G Network Slicing – C-SCRM Best Practices
- Ransomware Threats and Impacts to Industry
- Venture Capital and Supply Chain Vulnerabilities
April 2022 — Fortify the Chain
- April 2022 National Supply Chain Integrity Month press release
- April 2022 NSCIM calendar of events
- Agri-Food Supply Chain Spotlight
- Defense Industrial Base Supply Chain Spotlight
- Energy Supply Chain Spotlight
- ICT Supply Chain Spotlight
- Public Health Supply Chain Spotlight
- Transportation Supply Chain Spotlight
- Supply Chain Cyber Attacks
- Baker's Dozen - 13 Elements of an Effective SCRM Program
- Podcast: Securing U.S. Supply Chains - Addressing Our Vulnerabilities with Jeanette McMillian
April 2021 — A Call to Action
- Press Release: National Supply Chain Integrity Month – A Call to Action
- Software Supply Chain Attacks – 2021
- Supply Chain Risk Management: Best Practices in One Page – 2021
- Framework for Assessing Risks - 2021
- Sector-Specific Supply Chain Best Practices
Supply Chain Risk Management (SCRM) - Don't Be the Weakest Link!
- NCSC SCRM Best Practices
- Intelligence Community Logistics and SCRM
- NCSC Supply Chain Risk Management video
- 2018 Foreign Economic Espionage in Cyberspace report
- NCSC Federal Partner Newsletter: National Supply Chain Integrity Month
- MITRE report: Deliver Uncompromised
Supply Chain Risk Management
Executive Orders
- EO 13636 Improving Critical Infrastructure Cybersecurity
- EO 13806 Assessing and Strengthening the Manufacturing and Defense Industrial Base and Supply Chain Resiliency of the United States
- Executive Order 13806 Report
- EO 13873 Securing the Information and Communications Technology and Services Supply Chain
- EO 13913 Establishing the Committee for the Assessment of Foreign Participation in the United States Telecommunications Services Sector
- EO 13984 Taking Additional Steps to Address the National Emergency with Respect to Significant Malicious Cyber-Enabled Activities
- EO 14005 Ensuring the Future Is Made in All of America by All of America's Workers
- EO 14017 America's Supply Chains
- EO 14024 Blocking Property with Respect to Specified Foreign Activities of the Government of the Russian Federation
- EO 14028 Improving the Nation's Cybersecurity
- EO 14034 Protecting Americans' Sensitive Data from Foreign Adversaries
Authorities, Policies, and Standards
- SECURE Technology Act: Establishment of the Federal Acquisition Security Council
- NIST Special Publication: Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations (May 2022) (NIST SP 800-161r1 PDF)
- DNI ICD 731 Supply Chain Risk Management for the Intelligence Community (PDF)
- DNI ICS 731-01 Supply Chain Criticality Assessment 20151002 (PDF)
- DNI ICS 731-02 Supply Chain Threat Assessments 20160517 (PDF)
- DNI ICS 731-03 Supply Chain Information Sharing (PDF)
- DNI ICS 731-04 Supply Chain Vulnerability Assessments (PDF)
- DNI ICS 731-05 Supply Chain Risk Assessments (PDF)
Tools
Reducing Threats to Key U.S. Supply Chains
- NTIA Releases Minimum Elements for a Software Bill of Materials
- NCSC Supply Chain Risk Management Tri-Fold: Reducing Threats to Key U.S. Supply Chains (PDF)
Podcasts
- Authorized Disclosures Podcast: Cyber and Supply Chain Security Discussion with ONCD
- Podcast: Supply Chain Security Discussion with CBP
- Podcast on How One Federal Program Worked to Enhance its Supply Chain Security
- Podcast on Cyber & Supply Chain Threats to the Health Care Sector
- Podcast: Securing U.S. Supply Chains - Addressing Our Vulnerabilities with Jeanette McMillian
Additional Resources
Insider Threat
NCSC co-leads the National Insider Threat Task Force (NITTF) with the FBI. The NITTF helps the Executive Branch build programs that deter, detect, and mitigate actions by insiders who may represent a threat to national security. The NITTF develops guidance, provides assistance, assesses progress and analyzes new and continuing insider threat challenges. It is important to note that insider threat programs target anomalous activities, not individuals, so the NITTF’s work is coordinated with the relevant organization’s records management office, legal counsel, and civil liberties and privacy officials to build-in protections against infringing upon employees’ civil liberties, civil rights, privacy and whistleblower protections.
Insider Threat Websites
- National Insider Threat Task Force (NITTF)
- FBI Counterintelligence
- Defense Security Service (DSS)
- CERT Insider Threat Center
Relevant Reports, Briefings & Reading Material:
Economic Espionage
Throughout history, America's adversaries have routinely taken their competitive efforts beyond the battlefield. They frequently avoid using standing armies, shirk traditional spy circles, and go after the heart of what drives American prosperity and fuels American might. Nazi spies during World War II tried to penetrate the secrets behind our aviation technology, just as Soviet spies in the Cold War targeted our nuclear and other military secrets. Today, foreign intelligence services, criminals, and private sector spies focus their efforts on American industry and commerce.
These adversaries employ traditional intelligence methods against vulnerable American companies. However, their gaze has shifted to the cyber realm. The cyber environment, where critical business and technological information resides, provides a fast, efficient, and relatively safe avenue for penetrating the foundations of our economy. Their actions jeopardize intellectual property, trade secrets, and technological advancements vital for national security. Economic espionage against the private sector poses a long-term threat to U.S. prosperity.
Corrective action demands collaboration between the Federal Government and the private sector. Technologies nurtured by American minds and universities are at risk of becoming the spoils of competing nations. Unfortunately, the private sector alone lacks the resources and expertise to effectively thwart foreign attempts to pilfer critical American know-how.
Counterintelligence, not a typical corporate function, faces two challenges. One the cost. CI measures consume resources that could otherwise fuel growth. Second is the Nature of Public Corporations. Shareholders and growth ambitions drive American companies into developing markets, often leaving them vulnerable to espionage.
In this high-stakes game, vigilance, cooperation, and strategic investment are essential to safeguarding America’s future prosperity and security.





